As I make this site publicly accessible, it occurred to me that many of you will be getting warnings from your browser about the host SSL certificates not having a recognized certificate authority. Now, before I get into a techie rant (what I will also refer to here as a “Solar Flare”), here is a not so techie “here is how you fix it” post.
So, when you connected to a site such as this, rather than getting a pretty page, you likely got something like this…
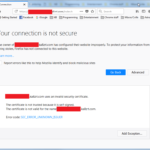
Now, if you are going to a site such as for you bank, going shopping at some big-name (or not-so-big-name) company’s site, etc., seeing this screen is like coming to a stop-sign to cross a busy 4 or 6-lane highway, where traffic is doing 65MPH… the mind should go “Danger! Danger! Danger Wil Wheaton!” (Yea, I know… mixed memes, but…I could not resist, as a soon to be written post will tell you why.) The reason is that for your bank, or any reasonably sized company, the primary stumbling block for the certificates should be a non-issue, and that stumbling block is the cost. More on that in a moment, but in this case, how do you fix it for this site? And the answer is simple, and just involves going to another site, clicking on a link, and accepting/trusting a couple of certificates there. And that site is www.cacert.org. On their main page, up at the top, they have a link labeled Root Certificate, where with a few clicks, there is no more warning. They even have a number of Wiki articles about this process, such as ImportRootCert where they go into trusting their certificate, so that mine and others like it don’t give you the warning to begin with.
Now, for those who are interested, please allow me to snag my soap box….
and while I do, let me start out by saying that regardless of what it may sound like, I am a firm believer in SSL and what comes with it. But like I would rather go to say Ohio or even travel around town to get groceries by car rather than by horseback or horse and wagon, just as cars have some massive downsides which could be improved (pollution and cost being the top two), there are some issues, sometimes huge, with SSL certificates.
SSL certificates, if you were not aware, are the high-tech way in which things such as web-sites can present an ID which your browser can look at and say “OK… you are who you claim you are.” It is kinda like presenting your driver’s license when making a big purchase in a store, only maybe a touch better. How many of you would recognize the driver’s licenses for a different state? Myself, even though I lived for much of my adult life in Ohio, could not look at what might be a driver’s license and say for an absolute certainty that it was valid. The same is true for Pennsylvania, even though it was far more recently that I lived there. I wonder how many officers for say CHP, VSP or other state or local agencies could do it visually, which is perhaps part of why they call dispatch with your license info when you get pulled over. But rather than having to contact a central authority, what your browser does is this. The certificate which a web site presents to your browser when they start talking contains a whole wealth of information, such as the hostname or IP address, what uses for which the certificate is valid, an expiration date, a certification “stamp”, and what is known as a public key, which is used for validating the connection and later communications. The public key goes along with a private key which the site works hard to protect, and the certification stamp on the certificate was created with a similar private key which the “certificate authority” (CA) supposedly protects as well, just like your local notary keeps their “stamp” or “embosser” secure. But it all relies on what is known as “Asymmetric” or “Public-key” encryption, where through the use of complicated maths involving huge numbers, I can use one number to either encrypt or sign an electronic document, and you can use a number which matches to decrypt the document or authenticate the signature. Feel free to follow the links or drop me a message if you would like to talk more about it, but the huge question remaining is… how do I get the public key for some site (or even a certificate authority), and know that it can be trusted?
My soap box…
The trick is, with your browser or operating system, somewhere in all the bits and pieces which get installed, you have a list of public keys for the certificate authorities (CAs) I have been mentioning. Think of it as having a booklet with a list of all the stamps and signatures of key notaries out there, with a way to look up and see more pages, with each page itself notarized by one or more individuals in your booklet, either directly or indirectly. But unlike just having a spot on the page where the page is embossed or stamped and signed, and you don’t know if a word was possibly changed or added, here the entire document, made up of a long string of 0’s and 1’s, can be “stamped” in such a way that changing anything in that string will, in near certainty be detected. Indeed, the digital form is like the old style wax seals which were common in the Middle Ages, only more so. (Encryption works in a similar way, but is a bit more complex). And there is quite a bit which goes into determining who ultimately gets into that “booklet”. Part of it is trust… such as, can I trust them to keep their private key secure? Can I trust them to go through all the right procedures to verify the information before they sign the certificate saying that this is the real “Wil Wheaton”? Seems kinda like the 50s-70s game show, To Tell the Truth, doesn’t it?? And therein resides a lovely little industry similar to the military industrial complex President Eisenhower warned us about. How little? Try more than $1 billion (yes, with a B) according to one report in 2016, with projections to exceed $3 billion by 2020. And this is, in part driven by effort’s such as Google’s “HTTPS Everywhere” effort, where more and more, sites without SSL certificates will be “shamed” or worse.
The dirty secrets…
Because many places which will “sign” SSL certificates used to prove a site’s identity can charge $100 or more per year for just a few minutes work to do what amounts to electronically notarizing, the cost of getting an SSL certificate and keeping it up-to-date is more than what some blogger (such as Wil?), or even an IT professional such as myself can justify spending. In a quick check, I found some of the big names such as Verisign and Thawte (both now owned by Symantec) charging nearly $400/yr for a certificate to “protect” a single hostname (such as ‘cinnion.ka8zrt.net’) while not protecting any others even in the same domain. And historic vendors such as Network Associates, now McAfee (yes, as in John McAfee infamy, among others) were as bad or perhaps worse. And while there are places which charge less, it remains a cash cow being milked in a huge way. And yet, what does a company such as Symantec get you for the cost of the certificate? For a blogger and their readers, it is not that big of a deal. It is true even for myself and this web site, though I will likely put up some interesting spots which will go beyond what is in place at the moment. The point where it becomes a thing for me, and hence my awareness of the dirty secrets, is I am a computer professional who has been working with the web since the transition from services such as Gopher in early 1993, and as such, I am supposed to know how to set up secure web sites, and using SSL is a part of that. But for a bank or someplace such as Amazon, they need to know that they and their customers are protected, and the same is true for us as individuals doing business with them. And supposedly, this means that we can TRUST the CA.
There I go again with those TRUST waves (Name that movie!). Does the CA take steps to protect us, such as checking the information for someone requesting a certificate, take the time to do audits of their processes and servers, and the countless other things involved to make sure that things stay secure? And going along with this… can we trust the browsers to do what is needed to validate that a certificate is still valid beyond not having passed its expiration date. At times, this is like walking into the grocery and buying hamburger and lettuce for your weekend cookout, but ending up in the hospital due to E.Coli contamination, such as the multi-state breakout of E. Coli O157:H7 affecting romaine lettuce we are seeing in the news which has resulted in multiple deaths. And like with that, the answer is sometimes no, as seen in a number of incidents such as one where Network Associates/McAfee had their intermediate signing certificate compromised, and the resulting problems it revealed This is why companies sometimes resort to purchasing SSL certificates such as this. Yes, you are seeing almost $1500 per year, and I do not know if they limit the number of servers under that certificate… as they sometimes do. But along with that trust is the fact that the CA is willing to back that up with a warranty, so that if something happens, they can pay out, sometimes in a big way (I have seen warranties for $1M or more for some certs). And aiding all this was how Mozilla (e.g. Firefox), Microsoft and others were controlling how a CA doing everything right could not get on their trusted CA list, while countless others, such as Verisign, Comodo, DigiNotar, GlobalSign and many others remained on the list. Add in some of the other mistakes, such as a CA revoking a certificate which results in tens of thousands of sites with their SSL connections reported as being untrusted, and you start wondering what many a developer has asked himself, sometimes at 3am after finding a bug which needed fixed when they started looking at things at the start of their work day: How did this ever work?? And the answer is, you can have a crowd walk through a field of mines rigged to go off only when a single switch in one spot is stepped on, and sometimes, you could play a major football game on that field, and not have things go BOOM! But even if there was no BOOM! today, there will always be a BOOM! tomorrow.
So given all that, years and years ago, while still living up in Da’Burgh (Pittsburgh for those of you who are not Yinzers out there), I needed to set up things for some in-house testing, and rather than using a self-signed certificate (and creating my own certificate authority, just like how Verisign, Network Associates and all the others did), and then having to add the public root certificate to my browser, I opted to go with CAcert, so that if I had to go through things again, I did not have to setup another personal CA later. It has its limitations… right now, every 6 months, I have to go through and renew and replace all my server certificates, which is a little bit of a hassle given I have roughly a dozen different certificates in use right now, with most being used only within the confines of my home network. But as I get them synchronized, it simply becomes logging in, clicking a checkbox, clicking the “Renew” button, then doing some cutting and pasting. And as soon as I get a new version of the program I use to manage these certificates, xca, compiled, repackaged, and reinstalled on the machine where I manage everything to do with my certificates (private keys, certificate requests, signed certificates, etc.), I will turn things into a mostly automated process. Or, I may just move over to using Let’s Encrypt, since that project, which has major name sponsors such as the EFF, Cisco, Facebook, Google and others, is already in the list of trusted CA’s… I may pretty much just switch over, if things are as good as they are now seeming (they have made much headway in the past two years). Besides, my old not quite friend, more than acquaintance Rich Salz (or as he often signed in those days “Rich $alz” or just “r$alz”, when we were the admins of the two largest USENET news installations around) is a part of their TAB (Technical Advisory Board). And even if they are issuing only 90 day certificates, instead of the ~180 day ones I am currently able to produce (or the 2yr ones I hope to produce if I can ever meet up in person with a couple of certified assurers to get the points I need before I can take the assurer test myself, the use of ACME might offset what was two years ago a problem with a solution awaiting release of the tools.
Well, it is now after midnight here, and even though I was asleep until almost 4pm, it was light when I went to bed (around 7am), and I have an appointment I am either going to have to cancel or pay a nice chunk of $$ to keep, and while there is a bunch of unemployment I have yet to be able to access, due to them sticking it on a pre-paid card instead of direct deposit like I requested, and my not having received the card… as much as I really Really REALLY need to keep this appointment, having to use perhaps 15% of what I have left in the account right at the moment… yea… (gawd, I hope something comes through soon!! No paychecks and no insurance is like having nearly empty air tanks while floating alone in the vacuum of space at the midpoint between here and the Andromeda Galaxy/M31)
Oh… and as for all the Wil Wheaton references… that will become apparent in the next post, which I should have up sometime tomorrow… and will continue that last reference.

Important news!! While trying to set things up so that folks could use their Facebook logins to comment, like, etc, I found that FB refused to handle the CAcert signed certificates. As a result, I have spent this evening updating my configuration to use the Let’s Encrypt site to issue and renew my certificates for my webserver. We shall see how this works out, and I figure I still have some more work to do for FB, and have not even started with Google+, LinkedIn, or Twitter, or to remove the others from sharing, etc.